Patent Backed Bankruptcy Report
Company Background:
Riverbed Technology, Inc. develops application performance infrastructure solutions in the Americas, Europe, the Middle East, Africa, and the Asia Pacific. The company offers Riverbed Application Performance Platform that ensures applications performance as expected, data is available when needed, and performance issues are diagnosed and cured before end users even notice. Its platform enables enterprises visibility to deliver, control, and optimize IT resources across the hybrid enterprise. The company’s products include application acceleration products comprising wide area network optimization products consisting of Riverbed SteelHead and Riverbed SteelFusion; Riverbed SteelApp virtual application delivery controllers; Riverbed SteelConnect, a software-defined wide area network solution to simplify and streamline the process of designing, deploying, and managing distributed networks; SteelConnect EX, a WAN edge infrastructure solution with SD-WAN for networks; and SteelStore cloud storage delivery products. It also offers Riverbed SteelCentral, a performance management suite; Riverbed Xirrus Wave 2 AP, a Wi-Fi access point that enables organizations to support business-critical applications in mobile environments; and Riverbed SaaS Accelerator, a solution that accelerates the performance of SaaS apps, such as O365, Salesforce, ServiceNow, and Box. The company sells its products to manufacturing, finance, technology, government, architecture, engineering and construction, professional services, utilities, healthcare and pharmaceuticals, media, and retail industries through value-added resellers and distributors, service providers, systems integrators, and field sales force. Riverbed Technology, Inc. was formerly known as NBT Technology, Inc. and changed its name to Riverbed Technology, Inc. The company was incorporated in 2002 and is headquartered in San Francisco, California. It has research and development facilities in Bengaluru, India; and the United States. Riverbed Technology, Inc. operates as a subsidiary of Riverbed Holdings, Inc. On November 16, 2021, Riverbed Technology, Inc., along with its affiliates, filed a voluntary petition for reorganization under Chapter 11 in the U.S. Bankruptcy Court for the District of Delaware.
Address
Ownership
Industry
680 Folsom St.San Francisco, CA 94107United States
Private
IT Systems and Software
Chapter Type | Case Number | Assets | Liabilities | Industry/Description |
11 | 1:2021bk11503 | $1 Bil – $10 Bil | $1 Bil – $10 Bil | IT Systems and Software |
Portfolio Valuation Range | Asset Valuation Range | Total Assets Valuation Range | Liability Range | Leverage Ratio Range |
$4.925 Mil – $19.7 Mil | $500 Mil – $10 Bil | $504.925 Mil – $10.02 Bil | $500 Mil – $7.5 Bil | 0.06732 – 20.0394 |
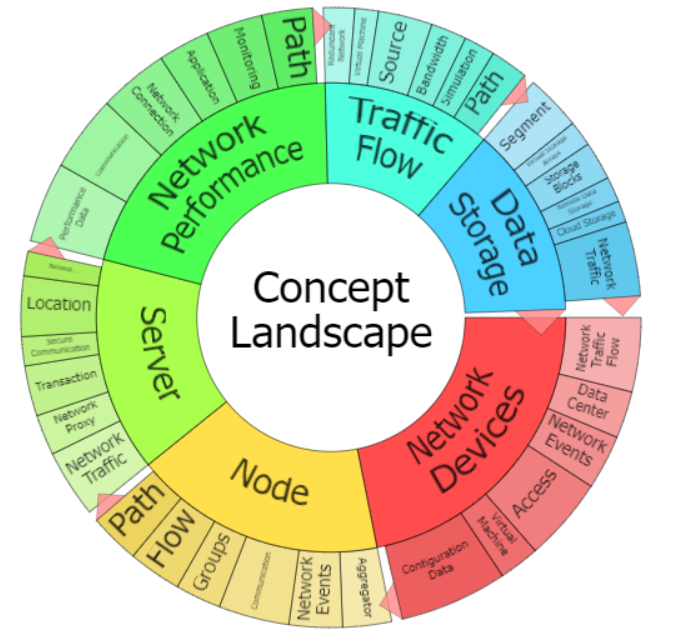
Patent Portfolio Breakdown
197 Active US Patents
Featured Assets
Abstract:
A single-ended optimized storage protocol enables storage clients or other devices to direct a remote data storage to copy data. In response to commands
via the protocol, a remote data storage can copy portions of a data stream at the remote data storage to destination storage locations within the same or a
different data stream. The protocol may be utilized for optimized transfer of data via a network to a remote data storage. An initial data stream is divided
into segments. Redundant segments are removed from the data stream to form an optimized data stream, which is transferred to the remote data storage.
Commands are issued to the remote data storage using the protocol to direct the remote data storage to reconstruct the initial data stream at the remote data
storage using the optimized data stream and optionally segments from other data streams previously transferred to the remote data storage.
Claim 1:
A method of transferring data to a remote data storage, the method comprising:
dividing, at a first network location, at least a portion of a first data stream into segments;
identifying a first segment in the first data stream that is a duplicate of a second segment in a second data stream, wherein the second data stream is stored in a
remote data storage at a second network location;
removing, at the first network location, at least the first segment from the first data stream to form an optimized data stream;
recording, at the first network location, an identity and location of at least the first segment within the first data stream;
transferring the optimized data stream from the first network location to the remote data storage at the second network location;
generating, at the first network location, a copy command that at least identifies the second data stream, a source location of the second segment within the second
data stream, a source length of the second segment, and a destination location of the removed first segment within the optimized data stream, wherein the
recorded identity and location of the first segment within the first data stream is used to generate the copy command; and
sending the copy command from the first network location to the remote data storage at the second network location, wherein the remote data storage executes the copy
command which causes the remote data storage to copy the second segment from the source location in the second data stream to the destination location in
the optimized data stream, thereby reconstructing the first data stream in the remote data storage at the second network location without transferring any
portion of the optimized data stream or the first segment back to the first network location, and wherein the remote data storage does not require an
optimization device to reconstruct the first data stream.
Abstract:
Network traffic information from multiple sources, at multiple time scales, and at multiple levels of detail are integrated so that users may more easily identify
relevant network information. The network monitoring system stores and manipulates low-level and higher-level network traffic data separately to
enable efficient data collection and storage. Packet traffic data is collected, stored, and analyzed at multiple locations. The network monitoring locations
communicate summary and aggregate data to central modules, which combine this data to provide an end-to-end description of network traffic at coarser time
scales. The network monitoring system enables users to zoom in on high-level, coarse time scale network performance data to one or more lower levels of
network performance data at finer time scales. When high-level network performance data of interest is selected, corresponding low-level network
performance data is retrieved from the appropriate distributed network monitoring locations to provide additional detailed information.
Claim 1:
A method of collecting and aggregating distributed traffic network data, the method comprising:
collecting first and second packet traffic data from first and second network locations, respectively;
storing first and second packet traffic data in first and second data storage devices at the first and second network locations, respectively;
generating first and second summary network traffic data at the first and second network locations, respectively, wherein the first and second summary network traffic
data is at a first time scale coarser than a time scale associated with the first and second packet traffic data;
communicating first and second summary network traffic data from the first and second network locations to a third network location;
storing the first and second summary network traffic data at the third network location;
wherein the first summary network traffic data includes first references adapted to retrieve at least corresponding portions of the first packet traffic data from
the first network location and the second summary network traffic data includes second references adapted to retrieve at least corresponding portions of the
second packet traffic data from the second network location; wherein
the first summary network traffic data includes an attribute common to at least a portion of the first packet traffic data; and
wherein the first summary network traffic data includes an aggregate attribute of at least a portion of the first packet traffic data.
Abstract:
A local network traffic processor and an application are resident on a common computer system. The application is configured to trust a server certificate issued by a local
network traffic processor, the local network traffic processor operatively being paired with a remote network traffic processor. A proxy server certificate, generated using identification information of a server associated with the remote network traffic processor and signed by the local certification authority, is used to establish a secure session between a local network traffic processor and the application.
Claim 1:
A method comprising:
determining that a local network traffic processor and a networked application are installed on a common trusted host;
in response to the determination, configuring the networked application to trust a server proxy certificate generated, using a server identifier, for a server
associated with a remote network traffic processor that is issued and signed by a local certification authority unique to and associated with the local network
traffic processor, the local network traffic processor operatively being paired with the remote network traffic processor to perform a network traffic processing function; and
using a proxy server certificate to establish a secure session between the local network traffic processor and the networked application.
.


